
The potential and security of blockchains
There are great hopes for using blockchain technology to enable "smart contracts" ※ that automate the processing of contracts, but there are also increasing concerns about security risks. We asked Teruhiro Tagomori of NRI SecureTechnologies about what specific risks there are.
The great potential of blockchains and smart contracts
The blockchain technology that supports the popular Bitcoin virtual currency has been gaining attention. This technology is a system that uses encryption and distributed networks to distribute and record information in a format that prevents modification, and is also referred to as distributed ledger technology.
Blockchains are a versatile technology that can be applied in a wide range of fields. Mr. Tagomori gives swap deals as one example of a technology where blockchains can be utilized.
"Smart contracts are a kind of blockchain technology that enable contracts to be automated. These smart contracts enable, for example, interest rate swap deals by automating the process to swap at a certain interest rate on a certain day."
A smart contract is a program executed on a blockchain. It enables the content defined in a contract to be described as a program that automatically executes that contract.
However, we need to be careful of the vulnerabilities of such smart contracts (programs) running on an open blockchain that can be joined by an unspecified large number of persons connected to the Internet. In July 2017, virtual currency worth approximately 3.4 billion yen was stolen from the blockchain platform called Ethereum. A vulnerability in a smart contract enabled an attacker to withdraw the virtual currency in a smart contract without authorization.
Mr. Tagomori stresses that although conventional applications (programs) such as Web applications also have vulnerabilities, there is a critical difference between them and the vulnerabilities of smart contracts.
"With something like a Web application, even if a vulnerability is discovered, the service can be closed and the application fixed to prevent perpetual attacks. However with a smart contract, the program cannot be modified after release, and this means it will perpetually be at risk of attacks once a vulnerability is discovered."
How should we confront smart contract vulnerabilities?
Mr. Tagomori says that there are various patterns of smart contract vulnerabilities. One example is the case where another smart contract can be called from a smart contract.
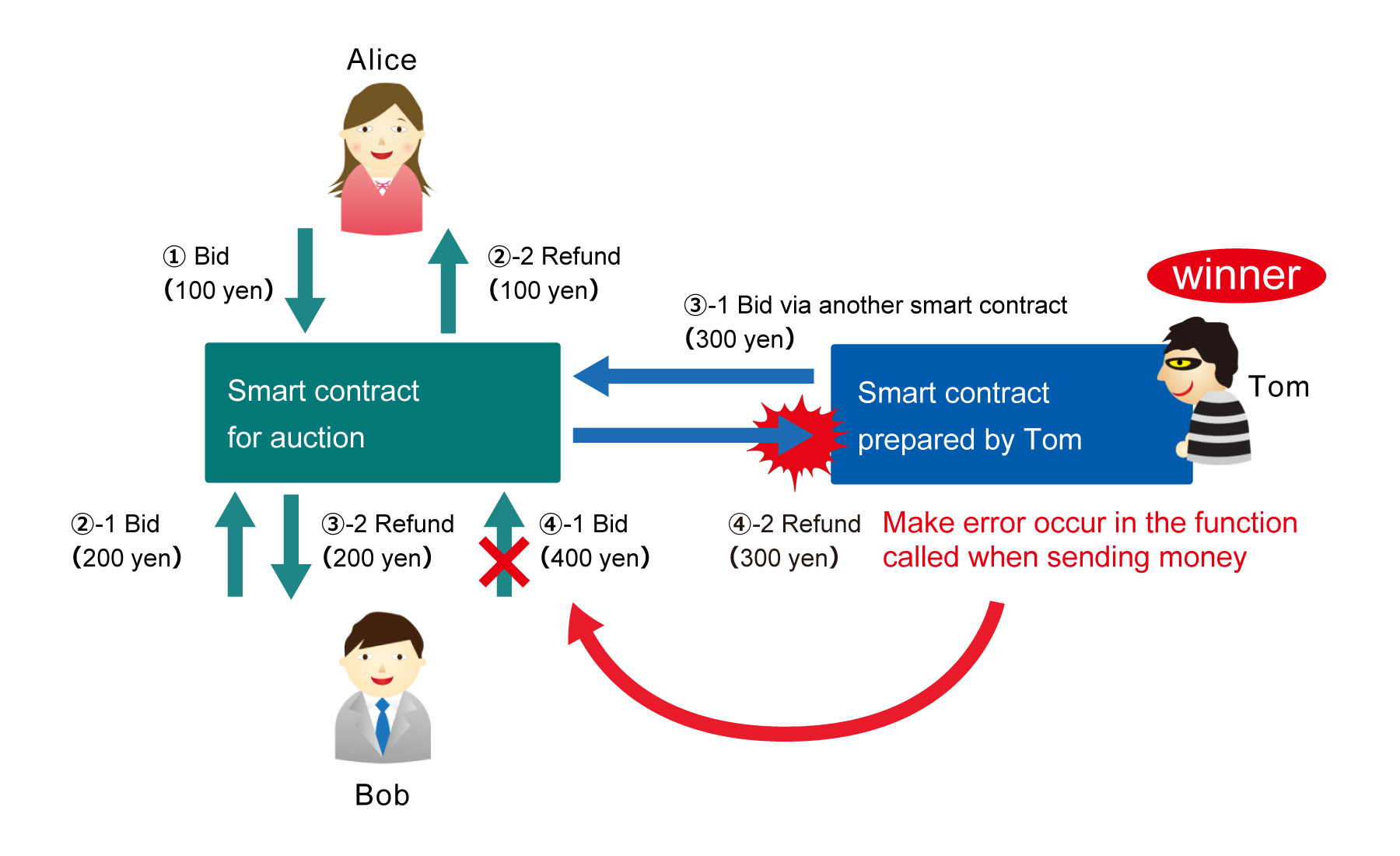
For example, let us say that a smart contract is used to process an auction. One participant named Alice sends money worth 100 yen to the smart contract to make a bid (1). Another participant named Bob makes a bid worth 200 yen (2-1). Since Bob is now the highest bidder, the smart contract automatically returns Alice's money (2-2).
Where a problem can occur is when a bid is made via another smart contract. Let us say that Tom makes a bid worth 300 yen via a smart contract he prepared (3-1). 200 yen returns to Bob at this time (3-2). Let us say that Bob then makes a bid worth 400 yen (4-1). The money that Tom bid is attempted to be sent back to the smart contract prepared by Tom (4-2), but if the function in the smart contract that is called when sending money has a process that deliberately causes an error, Bob's bid will fail due to that error. In other words, no one else will be able to make a bid, and Tom will definitely win the auction. "When developing smart contract programs, the possibility of such vulnerabilities being inserted needs to be taken into account," says Mr. Tagomori.
In the world of Web applications, we have accumulated knowledge for preventing vulnerabilities and secure coding has been systemized to create programs with a high level of safety. However, there are still few developers of smart contracts, and knowledge on preventing vulnerabilities has not yet been accumulated. It is likely that smart contracts with vulnerabilities will be released and cause great damage.
Mr. Tagomori says that although it is important to eliminate smart contract vulnerabilities before release, it is also important to incorporate a system for minimizing the damage of vulnerabilities that may be discovered.
"As I have mentioned, discovering a vulnerability in a blockchain may lead to perpetual attacks. That is why it can be effective to incorporate a protective measure like an emergency stop button that enables all reception of all processes to be stopped if a vulnerability is discovered. It is also useful to have a specialist with knowledge on security to check the source code when a smart contract program has been created."
Although smart contracts are a technology with a lot of potential, they also have the potential to cause a lot of damage due to attacks if a vulnerability is discovered. These risks must be considered when using smart contracts.
- Programmed contracts that are automatically executed. Smart contracts are being considered for application in various fields that use contracts, such as securities settlements, real estate deals, and the sharing economy.
Related Articles
Profile
-
Teruhiro Tagomori
* Organization names and job titles may differ from the current version.