
A Different Kind of IoT Security ― Safeguarding Industry 4.0 from Cyberattacks
Recently cyberattacks have repeatedly affected factories, power stations, and other large-scale plants. In December of 2015 and 2016, the cyberattacks against power plants in Ukraine caused power outages and serious uproars. In this era where IoT (Internet of Things) is becoming a household buzzword, how should we conceive of security in the field of Operational Technology (OT)? To answer this, we asked Tatsuya Katsuhara, a senior security consultant at NRI SecureTechnologies (NRI Secure).
A New Cyberattack Risk, Brought About by the Spread of IoT
The technology behind IoT, which refers to a network of physical devices, equipment, and many other items connected to the internet, is already starting to be used in a variety of fields. The items most familiar to us could include wearable devices in the form of fitness bands or wristwatches, or our household appliances that can be used or can obtain data over our home networks. Connected cars—which use sensors to acquire various data like the vehicle state or surrounding road conditions and then collect and analyze this data over networks—can also be considered a type of IoT.
While IoT may be readily accessible to us, there’s another IoT world out there that we never see in our normal, day-to-day lives. This is the type of IoT that’s used in factories, power stations, and other large plant facilities. In particular, the latest efforts being made using this IoT technology in manufacturing is what’s being called “Industry 4.0”. Tatsuya Katsuhara describes the advantages of using IoT in factories and other such sites in the following way.
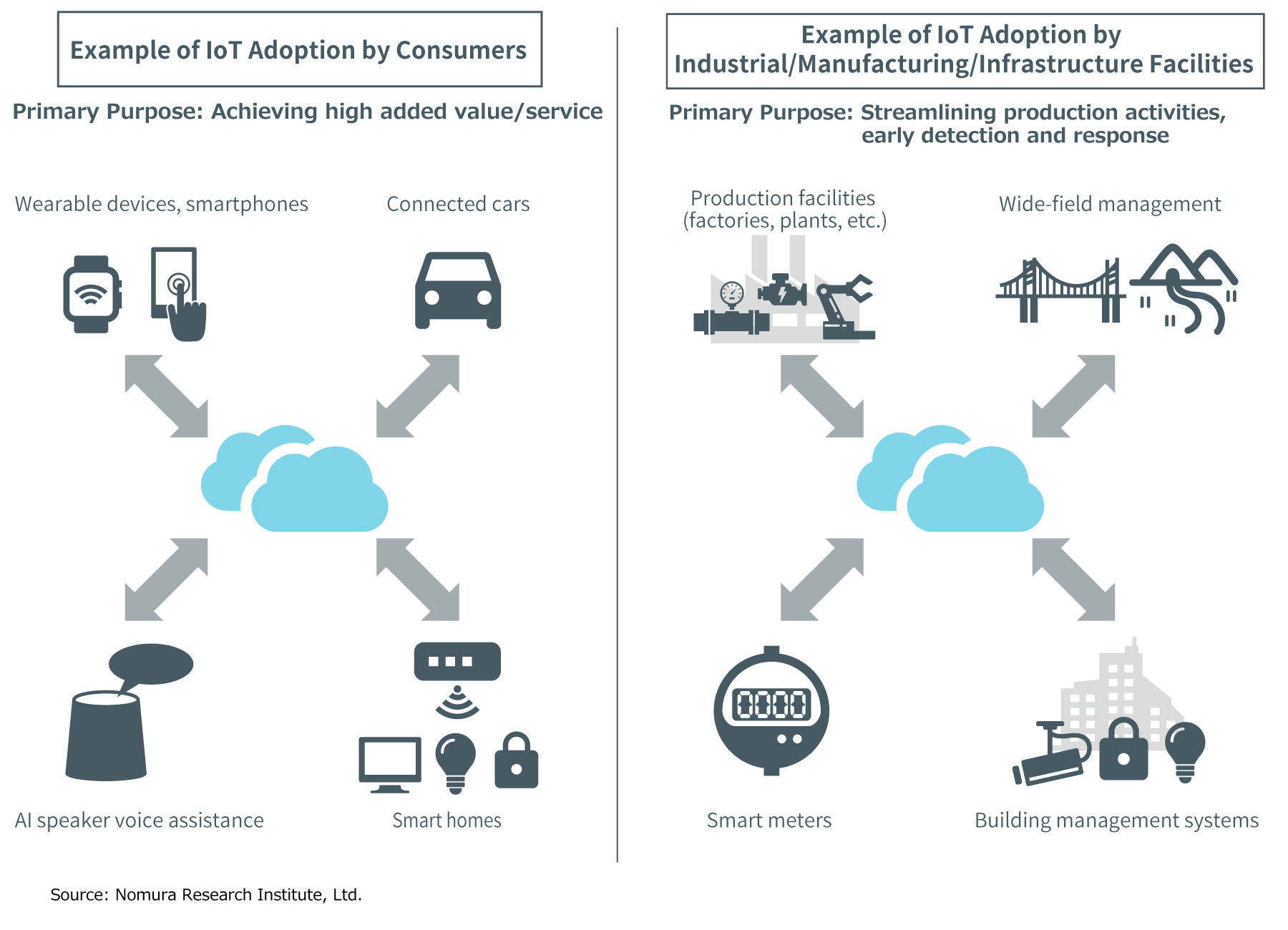
“When you can foresee equipment failures with IoT technology, it’s possible to replace the parts before they break down, and thus minimize the effects of stopping your factory line. There are other conceivable activities you can do as well, like making the use of your equipment more efficient to maximize your productivity, or analyzing the data you obtain from your IoT to create new value.”
What’s more, efforts are now underway that involve connecting IoT devices or control systems installed in factories and other facilities to the internet, in order to use an abundance of computing resources provided in the form of cloud services and thereby create new benefits. Katsuhara suggests that what we should consider is security.
“Conventionally we think that control systems in factories and other facilities could be reliably secured by cutting them off from outside networks,” he says. “But in reality, there have been more than a few security-related incidents where setting errors or operational circumstances have caused facilities to ‘inadvertently’ connect to an outside network, thus exposing them to malware or ransomware threats. Plus, there are more and more cases where in order to achieve greater efficiency or higher added value using IoT, part of your control system needs to be connected to the internet or some external network. That’s why control systems are at increased risk of exposure to cyberattacks that can exploit setting errors or system vulnerabilities.”文
Security in the OT Field Demands a Different Approach from IT Security
The technology we use to manage and operate control systems is referred to as OT (Operational Technology), and as Katsuhara points out, security for OT is vastly different from IT-related security.
“The IT world handles a lot of personal information, like information concerning financial assets, and confidentiality tends to be prized, but with OT availability is important. In many cases it involves social infrastructure such as electrical or water supply facilities, and the most important thing is continuously running these systems without halting operations. Another vital aspect to this is safety. People engaged in OT have been contemplating and pursuing safety for decades. It’s impossible to think about OT security if you neglect availability and safety.”
Given this background knowledge, it’s clear that IT and OT involve significantly different approaches to security. An obvious example would be a system update or installing antivirus software. Control systems have a very long operation period of 10 to 20 years, so older operating systems (OS) like Windows XP are still in use. In the IT world, an old OS can easily lead to security risks, and thus it’s recommended that they be updated immediately to a new OS. However, with OT, updating your OS could potentially cause the software you use for controlling your equipment to stop functioning properly, so you can’t simply run updates. Also, when you install antivirus software for dealing with malware onto your control system OS, there’s not only a chance of malfunction, but also the possibility you’ll cause processing delays. In an environment where devices are linked together in real-time on a millisecond level, even a slight processing delay could end up hampering normal operations. Sacrificing availability for your security measures would be defeating the purpose.
Regarding OT-related security, Katsuhara says, “if you think about it in terms of the principle of security, updating your device OS or installing antivirus software would be primary measures, as same as IT. But when actually these updates are difficult, you have to put effective security measures in place on multiple levels to control the risks. And while we refer to the OT field as a single entity, its characteristics vary widely from one industry to another. OT therefore requires you to take security measures from a different approach than what’s done in IT,” he says.
In fact, NRI Secure has already been sought out for consultations in cases where malware infections have brought a company’s production lines to a halt, or where a company has detected unauthorized access using malware.
Companies seeking to engage with IoT at their factories or other facilities could pursue the benefits from the secure use of IoT by considering security measures for defending against cyberattacks at the same time.

Related links:
-
NRI Secure in-depth article:
Views on Protection Required for “Tactical” Use of Industrial IoT(Japanese)
Profile
-
Tatsuya Katsuhara
* Organization names and job titles may differ from the current version.