“Encryption Key Management”: Supporting Information Security in the Digital Era
Currently, with the penetration of digital technologies such as AI and IoT and exchange of all information over the internet, encryption technologies are becoming indispensable for ensuring information security. One of the important elements of encryption is the data called “key”. If this is not properly managed, information security cannot be ensured. We interviewed Mr. Naoaki Suda, Mr. Hikaru Koizumi and Mr. Mai Asakura, the information security technology experts of NRI Secure Technologies (NRI Secure), about the importance of “key management” in the era of digital transformation (DX).
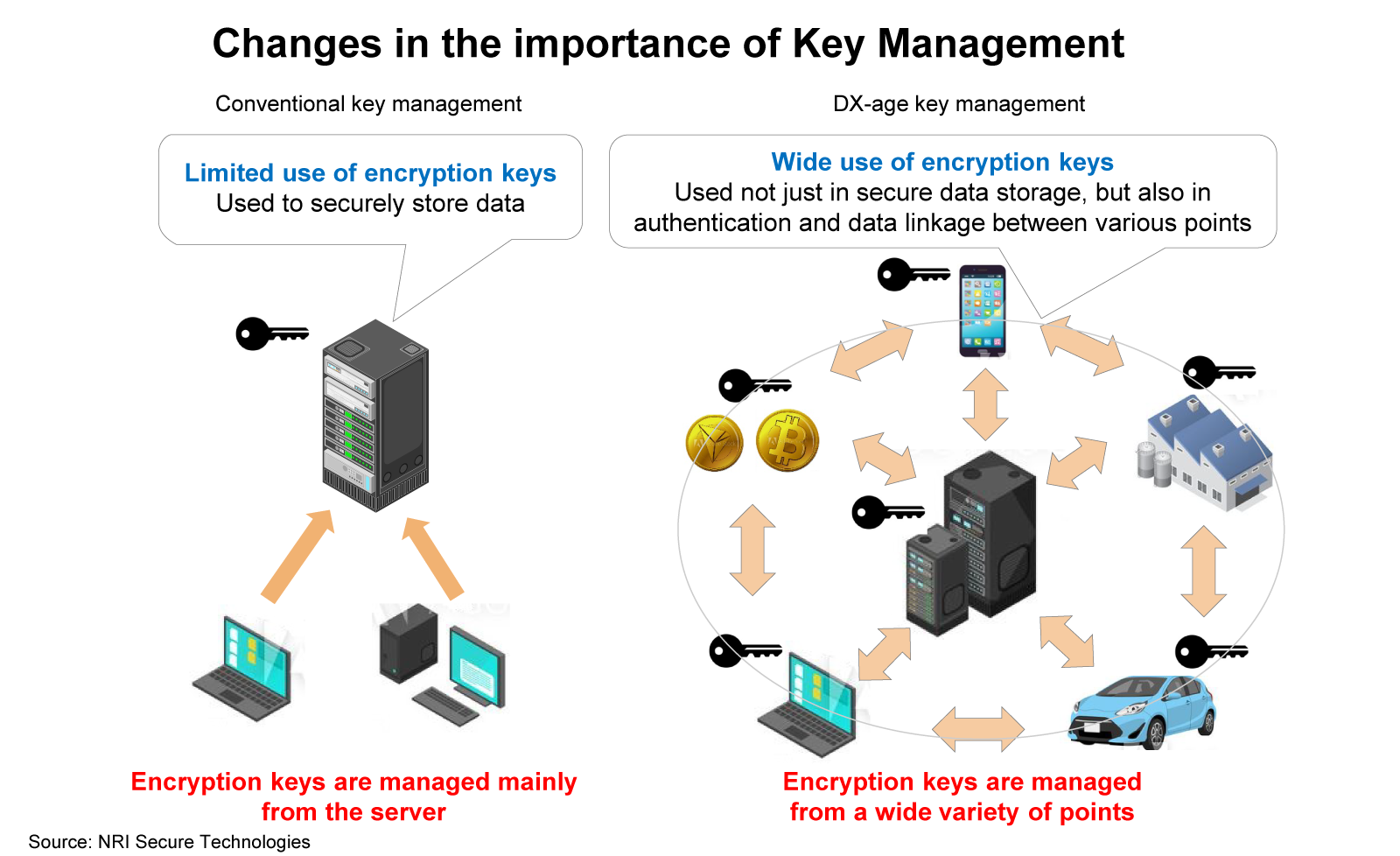
Appropriate management of “key” used in encryption is a social requirement
We are in an era where a vast amount of information including personal information is exchanged over the internet, and many things such as automobiles and consumer electronics are connected to the internet. In order to protect such data and ensure appropriate use of internet-enabled things, encryption technologies are gaining more importance than ever before.
On hearing the word ‘encryption’, many people tend to think of protecting the contents of communication and data from eavesdropping or interception. In addition to this, encryption technologies can help prevent tampering of communication contents and forgery by a third party.
“The data called Key plays a vital role in the use of encryption technologies,” says Naoaki, “and appropriate management of the key used in encryption is a social requirement”.
“In recent years, many standards have been set to ensure security, same as PCI DSS*1 in the credit card industry. Many of these security standards now even describe the concrete methods of key management. In order to respond to the requirements of a highly security-conscious society and ensure information protection and system safety, the key must be appropriately managed.”
Key management is a major issue in credit card payment process
As an example of a specific area where encryption key management receives attention, Mai talks about the transmission of credit card information.
“In recent years, P2PE (Point to Point Encryption) technology has been attracting attention in making credit card payments in franchise stores. In this form of encryption, the card details are encrypted in the store’s device and are sent in the same form to the center that processes the payment. With the introduction of solutions that comply with and are certified under the P2PE security standard PCI P2PE*2, it is possible to realize “non-retention”, which is equivalent to credit card information not being held by the franchise stores. Further, even in PCI P2PE, the encryption key saved in the payment device and the one used by the payment center need to be managed appropriately.”
The encryption key plays an extremely important role even in the virtual currency system that uses blockchain technology. Virtual currencies such as Bitcoin require the creation of a virtual “wallet”. The “wallet” does not manage the currency, but manages the encryption key (private key) required to handle virtual currency. Since this encryption key defines the so-called ownership for the virtual currency, it is important to strictly manage it. If this key happens to be stolen by a third party, the risk of the currency being used for payment or remittance to a third party will increase.
The management of the encryption key is a very serious issue especially in exchanges that deal in customers’ virtual currency such as bitcoin. For this reason, Hikaru talks about the need of key management from the operational perspective.
“As an information security measure for Bitcoin, it is possible to restrict use of the currency if the user does not have multiple keys. For this, multiple encryption keys can be created, which are maintained by different persons. In this form of management, even if one of these persons tries to commit fraud or carry out illegal operations, money cannot be transferred as the keys of the other persons are not available. If keys are held by multiple persons and they all keep a check on each other, there will not be any internal fraud. In this way, it is also important to consider a safe operation system for key management.”
Encryption technologies ensure safety for IoT
Encryption technologies are vital in the world of IoT as well. Besides encrypting the communication between the IoT device and the controlling server, encryption technologies are used to authenticate the validity of the IoT device connected to the controlling server.
Further, encryption technologies are used to ensure the security of connected cars. Naoaki explains, “Even after a connected car is sold, new update modules are required to be sent via the internet. Such data relates to the very core of automobiles; hence, it needs to be sent securely to avoid any tampering. Therefore, encryption technologies are used to encrypt the data or to verify that the sent update module is not tampered with”.
NRI Secure provides cross-industry services, such as support for development of an operation system, including system assessment and key management using encryption technologies, and support for conforming to PCI P2PE standard discussed above. Since encryption technologies are now used in a wide range of areas, we are receiving more and more inquiries with regards to our services.
The proper protection of clients’ personal information relates to a company’s credibility. For instance, when using IoT technology in automobiles and factory production lines, if there is a cyber-attack where the device is illegally controlled from the outside, it can impact human lives as well. In order to reduce such risks, it is expected that encryption technologies will gain more and more importance in the future.
- *1 Abbreviation of Payment Card Industry Data Security Standard. It is an international standard related to card information security created by PCI SSC (Payment Card Industry Security Standards Council, LLC.), which was established by five international payment brands, to protect the information of card holders.
- *2 Abbreviation of Payment Card Industry Point to Point Encryption. It is an international standard related to card information security created by PCI SSC (Payment Card Industry Security Standards Council, LLC.), which was established by five international payment brands, to certify compliance of P2PE solutions.
Related URL
Profile
-
Naoaki Suda
-
Hikaru Koizumi
-
Mai Asakura
* Organization names and job titles may differ from the current version.