
“Zero Trust”, the Next-Generation Security Model Supports DX and Work Style Reforms
With the emergence of new online services and an increase in the amount of information handled on the internet due to DX (digital transformation), public awareness regarding information security is also rising. In addition, more and more people are using PCs and smartphones from outside the company to access the internal network and cloud. As the way forward to deal with such changes, the Zero Trust information security model is currently in the spotlight. We spoke to Mariko Torigoe and Chizuru Arai of NRI Secure Technologies (NRI Secure) about this model and the benefits it can offer to companies.
Current IT environment and limitations of perimeter security
--With the advent of digitalization, new online services are being developed rapidly. In addition, teleworking (where employees work remotely from home or any suitable place) is also becoming increasingly popular. However, while the online activities of companies have increased, we find that their information security measures often hinder these transformations. Could you tell us about the challenges involved in the current information security measures?
Torigoe: The conventional information security measures of companies were based on the concept of "perimeter security". In other words, information security measures were mainly applied at the point where both internal and external networks meet, based on the assumption that the internal network (internet) is secured while the external network (internet) is not.
Arai: However, more and more people these days have started working outside the company’s internal network by co-working online with other companies and organizations, or working outside the office as workstyles diversify. Hence, there are many cases where data stored on the external clouds is accessed. Under these circumstances, only securing the network perimeter is not sufficient.
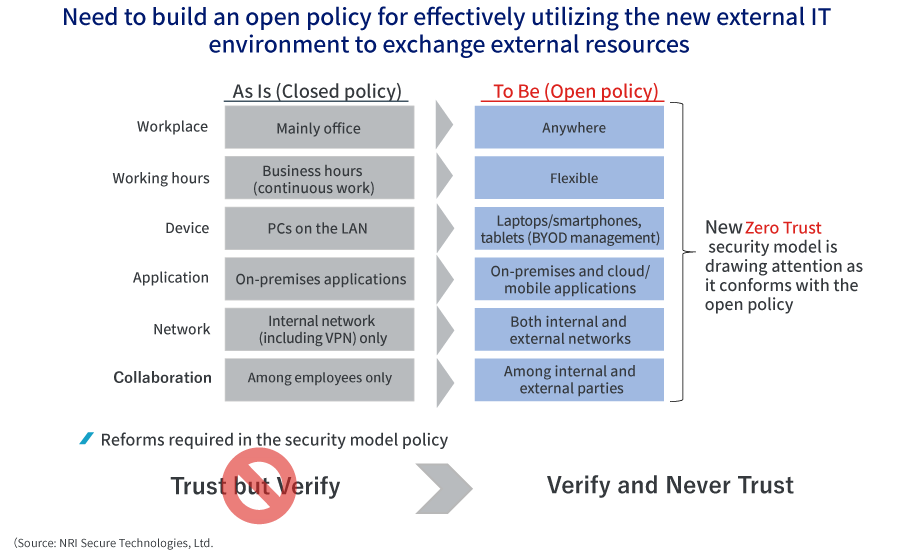
The foundation of Zero Trust model is "Verify and Never Trust"
--Do you think the new zero trust information security model can resolve these issues?
Arai: The guiding principle of perimeter security is "Trust but Verify", however, the zero trust model follows a completely different policy, i.e., "Verify and Never Trust”. In other words, the zero trust model is based on the premise of not trusting anything unconditionally; and because nothing is trusted, a more advanced verification system is required for everything, from users to network locations and devices in use.
"Digital Identity" is considered to be one of the most robust access management technologies that can realize the zero trust model. This technology determines whether to give access to users by not only checking attributes such as user ID and designation, but also various other attributes, including if the operating system is up-to-date with relevant security patches and if it is checked for viruses.
Torigoe: It is important to completely verify any access to the company’s data. The conventional information security models were mainly focused on network security, while the system to check access to data resources was imprecise and irregular. As the zero trust model does not rely on the boundaries of the internal network, it adopts a more robust approach to identity and security and properly verifies if the data is accessed by the actual user.
Zero Trust is also a cost-effective model
--What specific benefits can the zero trust model offer to companies?
Torigoe: Implementation of information security measures based on the zero trust model helps in creating an environment where user terminals (endpoints) can be protected even when the cloud services and internet lines are being used by many people From an overall IT perspective, it has reduced costs and shortened the implementation time as compared to establishing strong perimeter security. On the other hand, the management see it as an added benefit to security.
--Lastly, we would like to know the value that NRI Secure can provide in realizing the zero trust model.
Torigoe: As we don’t use vendors, we have substantial knowledge about information security solutions. Utilizing this knowledge, we try to compare multiple solutions to understand their features, specifications, and the environment that they fit in. In addition, we acquaint our clients with the product features mentioned in the specifications and help determine whether the products meet their requirements. We believe that the next-generation security models can vary depending on the client's environment. Our greatest strength lies in our ability to propose optimal solutions to clients that help them realize their own zero trust model.
Arai: Today, many companies are aiming to achieve digital transformation. Being a part of the NRI Group, we would not only want to support our clients in implementing relevant information security measures, but work together with them as a partner to support their entire business.
Profile
-
Mariko Torigoe
-
Chizuru Arai
* Organization names and job titles may differ from the current version.