
Information Security Risks and Countermeasures in the Age of Multi-Cloud
In recent years, many companies are increasingly using cloud services to support the use of IT in the corporate environment. Using cloud services has become the norm when building a new system, and companies often opt for "multi-cloud", which combines multiple cloud services. Satoshi Harada of NRI SecureTechnologies (NRI Secure) spoke to us about the security risks peculiar to such cloud environments.
Reasons for increased utilization of multi-cloud environments
Many companies are enthusiastically using cloud services because they do not require in-house servers or software, which reduces the burden of operations and management. Moreover, an increasing number of companies have been opting for “multi-cloud”, which allows one to combine various cloud services such as Amazon Web Services, Google Cloud Platform, or Microsoft Azure, with on-premises * environments that run their own servers.
Satoshi Harada of NRI Secure says, "Since each cloud service offers different functions, it is a common practice to select an appropriate combination of these services based on the company’s objectives. This is one of the reasons why multi-cloud environments are being increasingly used."
Another reason behind this trend is that business departments are using cloud services on their own without involving IT departments. Building a system in an on-premises environment requires complex mechanisms such as building servers and handling OS configuration, for which the involvement of the IT department is crucial. However, many cloud services are available with a purpose-built environment and can be used right away. Therefore, business departments can select cloud services as per their requirements.
Risk of massive information leakage due to improper cloud configuration
Harada points out that there are also information security risks associated with multi-cloud environments.
"Without proper configuration to protect the information, the risk of data leakage and breaches increases. Service providers and users are both responsible for information security. If users don’t implement the information security measures properly, information leakage and other accidents may occur. Moreover, using multiple cloud services or using a cloud service with multiple subscription accounts further increases the complexity of management and verification of configurations."
Harada further explains that cloud services have different information security risks than on-premises environments. For instance, accounts for using cloud services are hijacked, virtual servers are set up in the cloud to be used for cyber-attacks and virtual currency mining, and data stored on the cloud is leaked due to improper configuration. Harada warns that the risk of the latter type of information leakage is particularly high.
"For example, Amazon Web Services has a service called "Amazon S3" for storing data. This service has a mechanism for controlling access to data, but there have been many incidents where information was compromised due to improper configuration, making it accessible to anyone."
CWPP, CSPM to strengthen information security measures for multi-cloud environments
In a scenario where each department uses a cloud service suited to its own purpose, it is often the case that the respective cloud services all offer different functions and services. Ideally, each department should be responsible for making sure there are no security problems. However, as mentioned above, there have been many cases where a single misconfiguration led to a serious information leakage or system violation, and given the current availability of various cloud services, it would be difficult for each business unit to take full responsibility. As a way of avoiding such information security risks, IT departments can formulate a baseline for the use of cloud services. They can assess the use of cloud services by all departments and check whether information security measures and configurations are being implemented appropriately against the baseline. However, in the case of manual checks, it is difficult to check the usage status of cloud services and the details of information security measures thoroughly. As a solution to this problem, Harada recommends the Cloud Workload Protection Platform (CWPP) and Cloud Security Posture Management (CSPM).
"CWPP and CSPM are solutions that allow centralized management of security policies across clouds as well as across subscription accounts within the same cloud. CWPP provides a variety of information security features for workloads on various cloud services. On the other hand, CSPM is a solution that helps in continuously monitoring configurations and maintaining appropriate status, primarily for the range of operations available on the cloud service management screens. With these solutions, you can compensate for the deficiencies of each cloud environment and maintain a baseline of security measures by continuously evaluating cloud environment configurations."
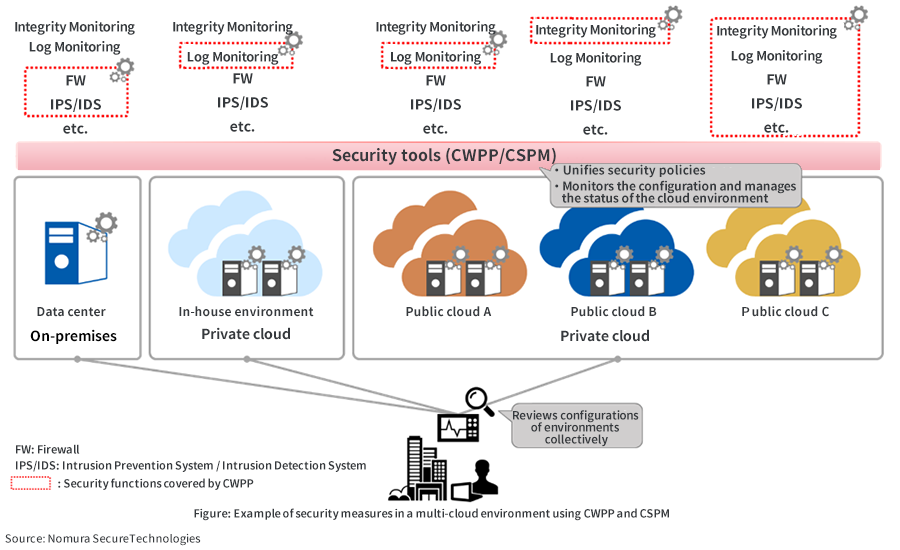
In addition to providing support with CWPP and CSPM installation, operation, and monitoring, NRI Secure also provides centralized monitoring of logs from servers and firewalls in cloud environments. Regarding this monitoring service, Harada says, "Events are examined by professional security analysts, and we believe that providing in-depth analysis and extensive protection 24x7 is our most distinguishing feature."
Going forward, if Digital Transformation (DX: the transformation of businesses using AI and IoT technologies) advances, the presence of cloud systems in the IT environment will increase more than ever, and multi-cloud services will also develop. Although cloud services certainly have great advantages, we must also be wary of the information security risks involved.

- *On-premises: Introducing, building, and operating server equipment and other items necessary for companies to use in-house information systems.
Profile
-
Satoshi Harada
* Organization names and job titles may differ from the current version.