
The Telework Security Demanded by the Post-Corona World
With the declaration of a state of emergency due to the spread of Covid-19, many companies have established telework environments to allow their employees to work from home. However, there have also been reports of numerous cyberattacks targeting telework environments that were created as crisis measures. We spoke with Jun Odashima of NRI SecureTechnologies, a business leader with deep knowledge in the field of information security, about the type of security that will be needed for telework in the after-corona world.
Companies can’t just say “It’s a VPN so it’s safe.”
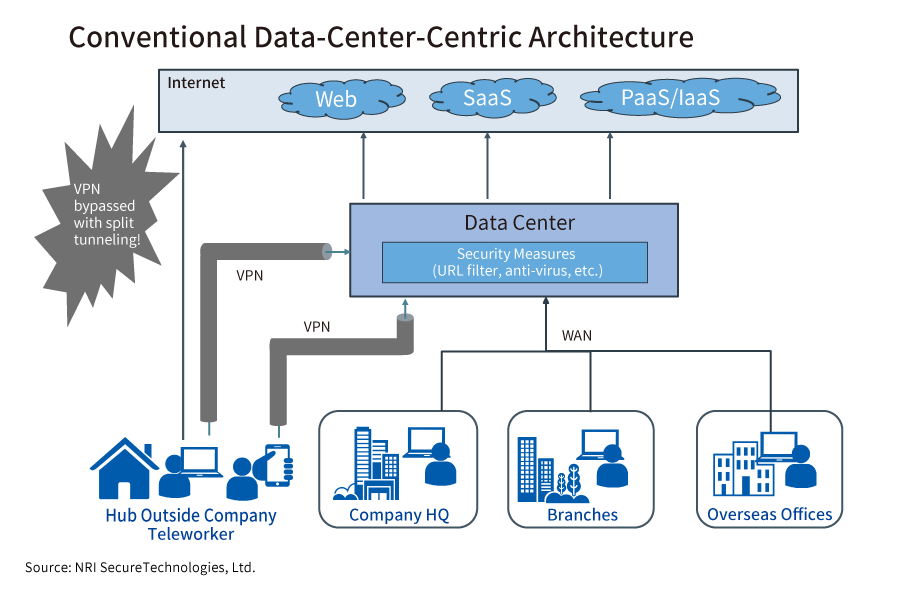
I believe the majority of telework involves using a VPN (virtual private network) to connect to a company’s LAN. On a VPN, data is exchanged by connecting a company’s entryway, which is usually installed in a data center, with a home PC by connecting through an encrypted communication tunnel. The encryption prevents eavesdropping on the content of communication, and the robust authentication performed when connecting to the VPN prevents unauthorized access by malicious third parties.
However, with VPNs, the “split tunneling” problem has been said to be an issue of concern for some time. When an employee connects to a company from a remote environment, the VPN connection is established after connecting to the internet through Wi-Fi (wireless LAN) or the like. “Split tunneling” is a setting whereby, at the time of connection, communication to the company travels via the VPN tunnel, but all other websites etc. on the internet are accessed directly without going through the VPN.
Because split tunneling does not consume bandwidth on company internet connection lines, it can seem at a glance like a good thing. But split tunneling also allows users to access the internet without utilizing the various security measures in place at companies, and thus carries an increased risk of malware infections and data breaches.
To solve this problem, companies should transition to a cloud-centric architecture, which works by keeping PCs connected to a security gateway in the cloud at all times to ensure security, and by allowing access to all locations, including those within the company, under those security conditions. This approach has been proposed by Gartner, Inc. as the new concept of SASE (secure access service edge). By forcing users to be constantly connected to a security gateway in the cloud, companies can strengthen security while minimizing the impact on performance.
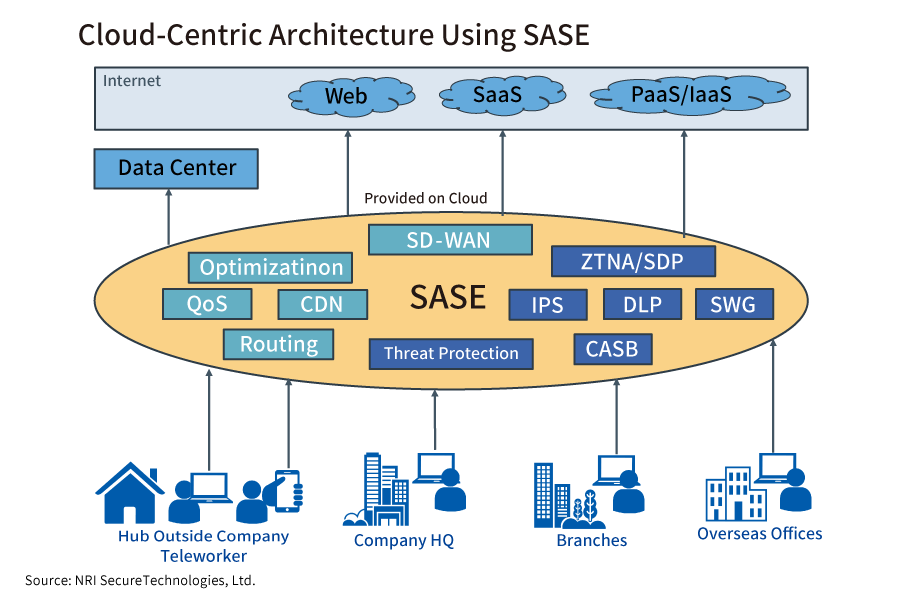
The most important aspect of both VPN and SASE is robust “user authentication”. The best way of achieving this is to implement “two-factor authentication”, which combines authentication by ID and password with authentication using a one-time password or the like.
Should PCs be thin client or fat client systems?
Client terminals can be thin client systems, in which terminal-side functions are kept to a minimum and applications are executed and managed on a server, or fat client systems, in which all storage media, application software and the like are provided on the terminal so that processes of all kinds can be executed on the terminal side, as in a conventional PC.
It is widely believed that thin client systems are superior from the standpoint of telework security because no information is left on the local terminal, but personally, I think it would be a waste if companies failed to utilize the ever-evolving computation capabilities of PCs and smartphones for data processing, document creation, programming, and other such activities.
Before you can even set up a thin client, you need to prepare a virtual desktop infrastructure (VDI), in which a desktop environment is virtualized and consolidated on a server. This involves substantial initial investment and running costs. In addition, since there may still be some lingering malware risk depending on the system, using a thin client system cannot be said to guarantee that local security measures are “unnecessary”.
In a fat client, by contrast, security reinforcements need to be implemented on the assumption that data containing confidential information will be handled on local PCs, smartphones, and other terminals.
One way of achieving this is to use the Windows standard BitLocker feature and the like to protect confidential and personal information by encrypting disk content. Furthermore, by using unified endpoint management (UEM), in which all devices owned by a company are managed and operated from a single management screen, it is possible to remotely delete terminal data at time of loss or theft (remote wipe function), and to strengthen security by, for example, restricting data removal via USB ports. Other effective methods include cloud access security brokers (CASB), which comprehensively manage security when cloud services are used, and network data breach prevention measures that utilize access control functions for SASE cloud services.
What “risks” have surfaced as a result of the rapid increase in telework?
According to a survey, since the Covid-19 pandemic, the number of computers have open communication “entryways” – in other words, SMB ports, a communication protocol used for Windows file sharing on the internet, and RDP ports, a communication protocol used when logging into Windows remotely – is increasing substantially.
This hints at the possibility that PCs which have been taken home by employees will be fully exposed on the internet. If a PC has lax security settings and an easy-to-guess login ID and password, it is at risk of unauthorized access by malicious third parties, which can lead to malware infections and data breaches.
If companies work from the assumption that they are lending telework PCs and smart devices, they can impose robust security settings such as utilizing UEM or the like to block SMB/RDP access. Furthermore, by monitoring terminals connected to their networks and introducing “EDR” software for discovering and dealing with unauthorized intrusions and malware infections, companies can create systems that will be rapidly responsive in the event of any trouble.
Many companies today have been forced to implement telework initiatives in response to Covid-19. We can now see that there are many information assets requiring protection, and that it is extremely difficult to realize ideal telework security without sacrificing productivity.
However, the attitude that “security incidents happen because of telework” is unacceptable. It is precisely because of the growing necessity of telework that companies need to get serious about strengthening telework security.

Profile
-
Jun Odashima
* Organization names and job titles may differ from the current version.