
Cyber-Attack Trends and Key Points for Countermeasures as Seen from the Front Lines of Security Log Monitoring
NRI SecureTechnologies (NRI Secure), a group company of Nomura Research Institute (NRI), provides a “Security Log Monitoring Service (NeoSOC)” that enables swift detection of cyber-attacks by monitoring the logs of various devices. In this article, Kazuki Amano and Yurie Tsutsui of NRI Secure, who have been involved in this service and are well-versed in cyber-attack trends, discuss recent security trends and the importance of log monitoring.
The Latest Techniques Used for Spreading Malware Infections
More and more companies are suffering damage from cyber-attacks, for instance by having their information leaked via unauthorized access to servers, or by being targeted by ransomware and having their files encrypted with a ransom demanded for their return. Security countermeasures are required to avoid this kind of damage, but since the techniques used for such attacks are continually evolving, it is necessary to properly take measures that align with the circumstances.
What kind of cyber-attacks are occurring these days? Amano shines the light on the damage caused by a malware called “Emotet” that spread between October 2019 and February 2020, and then experienced a second wave of spread from July 2020 onward.

“Emotet is a malware that is spread through the use of email. In December of last year, a large number of suspicious emails were sent with the subject “Bonus Payment”, and when people clicked on the URL in the body of the email or opened the attached file, they were infected by Emotet. The attack coincided with the time of year when bonuses are usually paid, and many people believed the email. The infection spread as a result.”
As a recent new trend, Amano further lists the method of attaching malware to an email in the form of a password-protected zip file.
“Since many companies use password-protected zip files when exchanging files, the fact is that these attacks are difficult to curb using extension controls. Since the text of the emails is also written in fluent Japanese and designed to have the appearance of a business exchange, we are seeing many cases of people inputting the password written in the email, opening a file in the zip file, and getting infected.”
In recent years, more and more companies are outsourcing the work of monitoring their security logs to security operation centers (SOC) that monitor the logs of servers, security devices, and computers used by employees to swiftly detect outbreaks or signs of cyber-attacks. Tsutsui, who is a SOC analyst at NRI Secure, points out that cases of malware infection are detected relatively frequently.
“At present, malware infection or attempted infection occurs, on average, about ten times a month. Ten times may not sound like a lot, but almost all of our customers using NRI Secure’s SOC have strong information security measures in place. Even with these measures in place, an infection or attempted infection is occurring at an interval of roughly once every three days. I feel this is quite frequent.”
Log Monitoring Achieves Swift Detection of Cyber-Attacks
In 2020, many companies started making use of telework as a measure against the spread of infection of Covid-19. Amano warns that devices for VPN used for employees to connect to the company network while working from home during telework have also become a target of attacks.
“We are increasingly seeing attacks using unauthorized access that takes advantage of the vulnerabilities in devices for connecting by VPN. Since these devices are arranged at locations where internet access is possible, they are easy targets for attacks if there are any vulnerabilities.”
Log monitoring is critical for preventing these cyber-attacks. Gathering and monitoring the logs of various devices and detecting the signs of a cyber-attack as quickly as possible allows companies to prevent the spread of damage.
Meanwhile, Tsutsui points out that it is not easy to establish a system for log monitoring.

“Since we never know when a cyber-attack will occur, we must continuously monitor logs, but it is not easy to build a system for doing so. Further, when actually checking logs, without fine-tuning so that the “important logs” for a company’s environment are defined and can be extracted, a huge number of unnecessary alerts may be issued, and continuous monitoring could lead to fatigue.”
NRI Secure provides its “Security Log Monitoring Service (NeoSOC)” in order to solve such problems. The service involves security analysts with high-level security qualifications, who are located in Japan, the U.S., and India, monitoring logs 24 hours a day, 365 days a year. Further, the service achieves high-level security management with no burden on the customer, such as by swiftly introducing new rules for detecting new cyber-attacks as they appear on the scene.
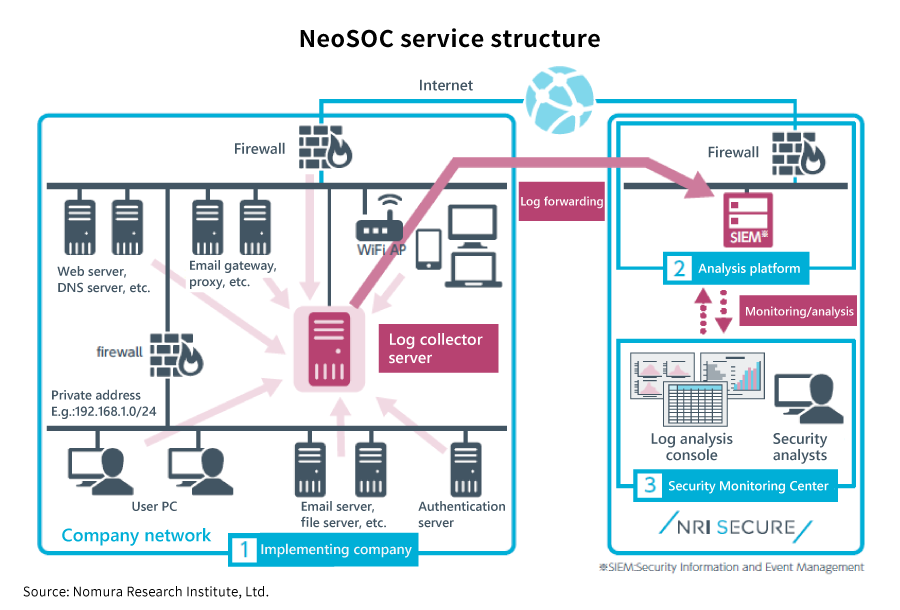
Tsutsui explains that NeoSOC is further engaged in an endeavor called “threat-hunting”.
“Threat-hunting is an activity that involves analyzing logs from a long-term perspective and checking whether any abnormality has occurred in order to discover threats that cannot be easily detected just by checking alerts in real time. We have increased our threat detection rate by combining this threat-hunting with correlation analysis for detecting threats by compounding a plurality of logs.”
Installing a device like a WAF (Web Application Firewall) is not the last step in security efforts. In addition to installing and operating the appropriate devices, it is necessary to design what kind of logs should be used as security monitoring measures to be continuously monitored. However, the reality is that it is difficult to establish a system for doing so and to employ personnel having security skills. It will become more and more important to make effective use of external resources in considering how to resolve such problems before serious damage by a cyber-attack occurs.
Profile
-
Kazuki Amano
-
Yurie Tsutsui
* Organization names and job titles may differ from the current version.