
Protecting Our Motorized Society from Cyber-attacks
"Connected cars," offering a variety of convenient functions, have become increasingly common in recent years. And as we approach 2020, self-driving automobiles, which operate based on their connection to advanced networks, will begin to be made available to the public. While advancements in ICT (information and communication technologies) have made the automobile an increasingly comfortable form of transportation, there is now the risk of cyber-attacks, which were not a factor in the non-connected automobiles of yesteryear. Here at NRI SecureTechnologies (hereafter "NRI Secure") we have anticipated this risk for over ten years, and have spent this time discussing ways to bolster security in order to keep automobiles safe. We asked Daisuke Noguchi, one of our consultants, what will be required to preserve the security of our motorized society.
The Threat of Terrorist Attacks, Theft, and Mischief
What kind of cyber-attacks are possible against automobiles, and what dangers do they pose? Noguchi discusses three possibilities.
"The first is terrorism. Unauthorized remote access would make it possible for a terrorist to take control of the steering functions of an automobile in motion, disable the brakes, or even just lock the doors so they can't be opened. Any of these attack scenarios could be a threat to human lives. The second possibility is theft. Criminals can alter the data in a car key to gain access and steal the car for themselves, or sell it abroad. Third are so-called pranksters, who might take control of a system to open and close people's car windows, or turn their indicators on and off, just as a 'prank.'"
Because these new automobiles are connected to a variety of external networks and devices like smartphones, attacker now have multiple new potential entry points in which to attack. If successful, an attackers who gains unauthorized access to certain key vehicle systems can even take control a vehicle's driving mechanisms. "It's like cars have become toys, turned into remote control cars," says Noguchi. "You can control remote control cars with a remote. Nowadays, you can unfortunately do the same thing with an actual car."
Implementing the "Automotive Penetration Test"
Automobile manufacturers have taken these new risks into account, and starting a few years ago, have begun working to address the increased dangers by establishing security groups within their companies. In May 2017, NRI Secure released our "Automotive Penetration Test," service aimed at giving automobile manufacturers the critical information needed to face these new security challenges. In this service, a NRI Secure specialist attempts to infiltrate a vehicle's systems to gain access that will provide them with control over the engine, brakes, door locks, and indicator controls, all done in an attempt to simulate the potential actions of a real attacker.
The cars are evaluated using broad and detailed criteria based on leading standards like the EDSA (an international standard for control equipment). Once completed, we report any vulnerabilities found within each automotive system, or with the car as a whole. We will then suggest possible solutions for the vulnerabilities so that the automobile manufacturer is able to take the steps needed to strengthen the security of their cars. (See image below)
Overview of the "Automotive Penetration Test" Service
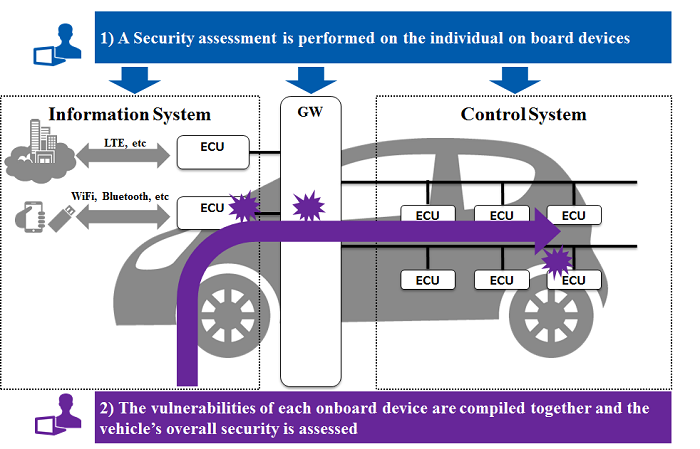
The equipment installed in automobiles can be classified into three categories: "information systems," which connect to external networks or devices, "control systems" like the brakes and steering wheel, which control the motion of the vehicle, and "gateway (GW)" technologies, which separate these two systems. If an information system is attacked by something like an external network, the attacker may infiltrate the control system via the GW, which could allow them to manipulate the vehicle.
The Need for a Continuous Monitoring System for Security
Though these types of security evaluations are effective, Noguchi says that continuous security monitoring will be what is important in the future.
"Until now, with regards to the product cycle, there was no real need to tweak anything on the automotive systems and equipment on cars that people had already bought, unless they were recalled. But now that cars are connected to networks, there is a need to preserve security throughout the life-span of the vehicle, even after it is in the hands of the consumer. Systems must be continuously monitored for issues like cyber-attacks, and there must be countermeasures in place against any issues. In this sort of circumstance, we believe that continuous 'monitoring,' to check whether any systems are under attack, will be of particular importance."
Utilizing Our Future-Oriented Experience in Various Fields, and the Strength of Our Team of Specialists
Connected cars will be in widespread use in the future, and are expected to comprise over 90% of the new cars that are sold in 2035. Self-driving cars will also become increasingly common as their technology becomes more refined, their range of use will increase, and many more of these cars show up on the road. As this occurs, the utilization of automotive systems and the number of external connections will increase along with the vehicle system technology becoming increasingly more sophisticated. All of this new technology and connectivity can broaden the attack surface and create an increased risk of the vehicle systems being exploited. Noguchi says that for this reason, "It is very important that we have a system to monitor car security. This kind of system will be an important part of the infrastructure to preserve safe driving into the future."
"So far, we at NRI Secure have provided one of Japan's only monitoring services in the field of information security. Over ten years ago, we began sounding the alarms about security threats to control system infrastructures for things like electricity, gas, and water. This was back when society still didn't understand the importance of such security, and since then, we have dedicated ourselves to providing security measures to handle these threats. We have also had many years of experience monitoring the information systems of financial institutions which are under the constant threat of cyber-attacks. We plan to utilize our many years of experience, which spans a great variety of fields, to help ensure safe driving in our future society."
NRI Secure is home to a team of ethical hackers that include former winners of world hacking tournaments, as well as the knowledge and technologies needed for the preservation of information security, and cultivated through our years of experience in various industries and fields. Our company will utilize these strengths as we dedicate ourselves to the realization of a safe, motorized society for the future.
If you are interested in knowing more, see the following for more information on the "Automotive Penetration Test" and our work at NRI SecureTechnologies.
NRI SecureTechnologies Official Website
Overview of the "Automotive Penetration Test"
Cyber Security Trend: Annual Review 2017

We compiled the "Cyber Security Trend: Annual Review 2017" based on data gleaned from the information security services offered in 2016 by NRI Secure. This report, the 13th of this series, organizes the data into three main categories, "External Threats," "Internal Threats," and "System Management," and provides analyses on these themes.